Review on the Application of Artificial Intelligence in Antivirus Detection System

Evaluation of Local Security Outcome Management System vs. Standard Antivirus Software
Institute for Research in Technology, ICAI Schoolhouse of Engineering, Comillas Pontifical University, 28015 Madrid, Espana
*
Author to whom correspondence should exist addressed.
Academic Editors: George Drosatos, Konstantinos Rantos and Konstantinos Demertzis
Received: 24 December 2021 / Revised: 17 January 2022 / Accustomed: eighteen January 2022 / Published: xx January 2022
Abstract
The detection and classification of threats in figurer systems has been one of the main problems researched in Cybersecurity. As engineering evolves, the tactics employed by adversaries have likewise become more sophisticated to evade detection systems. In consequence, systems that previously detected and classified those threats are now outdated. This paper proposes a detection arrangement based on the assay of events and matching the risk level with the MITRE ATT&CK matrix and Cyber Impale Concatenation. Extensive testing of attacks, using nine malware codes and applying three different obfuscation techniques, was performed. Each malicious code was analyzed using the proposed effect management organisation and also executed in a controlled environment to examine if commercial malware detection systems (antivirus) were successful. The results bear witness that evading techniques such as obfuscation and in-memory extraction of malicious payloads, impose unexpected difficulties to standard antivirus software.
i. Introduction
Antivirus software is the most mutual tool being used to protect the user's computer from malware attacks. In that location are other protections methods such as local firewalls and corporate firewalls that protect the end-user from being totally exposed to attackers or malware already running on the local network. Nonetheless, there are likewise many ways in which a piece of malicious software tin get access to a personal computer. All sophisticated software, such as the operating system, programs running on a personal computer, and even software running on firewalls or other hardware equipment, contains bugs or flaws that may cause these systems to act in unexpected ways. Although most bugs are non meaning on their own and do non pose a security risk, an assailant can take reward of certain bugs to write programs called exploits to increase their armory of attacking tools. By combining a series of exploits into an "exploit concatenation", information technology is possible to circumvent all the defenses ane-by-one until reaching the victim'southward computer to execute some kind of malicious software at that place. The fact that malware eventually reaches the stop-user computer highlights the importance of malware detection software running locally.
This paper proposes a detection strategy based on events generated by the arrangement and its corresponding mapping with Cyber Kill Concatenation and MITRE ATT&CK. The contributions of this paper are:
-
A framework has been implemented to evaluate threats based on the analysis of events and subsequent nomenclature in the Cyber Kill Concatenation and MITRE ATT&CK models.
-
Using dissimilar obfuscation techniques, a ready of malware samples has been built to evaluate the effectiveness of commercial antivirus systems and determine their detection and classification capabilities while dealing with obfuscated files.
For a better agreement of the contents of this paper, it was organized every bit follows: Section 2 describes all the elements that must be known to understand the methodology proposed in this paper; therefore, the classification of malware families, the electric current functioning of antivirus systems, the most mutual evasion techniques, and the threat nomenclature model used to analyze events are explained. Section iii describes the proposed methodology and its implementation. Section 4 describes the experiments performed and the results obtained and includes the comparison with several known antivirus systems. Section 5 analyzes the results obtained with the proposed methodology. Section 6 concludes this paper and presents hereafter works.
2. Review and Background Knowledge
The detection and classification of threats [1] in networks and calculator systems is an essential component for organizations. The objective is to be able to detect malicious programs (malware) that accept evaded protection layers being able to attain a server or a user system. The emergence of these malicious programs originates back to 1971, when Robert Thomas created the offset computer virus called "Creeper" [2,3]. Since then, the evolution in number of attacks and sophistication level has been amazing, with different types of malwares appearing for all known computer systems.
2.1. Malware Family Classification
However, malicious code has not simply evolved technically, merely also in terms of threat. They non just damage files or computer systems, every bit they used to behave in the 1970s and 1980s, but they are also used to spy, steal information, or demand monetary ransoms.
Viruses: Usually incorporated into existing software, they are activated when the user executes the software. Their consequences are diverse, ranging from slowing down the system to corrupting or deleting information [4,5].
Worms: Do non need, at first, user intervention and have the ability, in contrast to computer viruses, to self-propagate through the network [half dozen,vii].
Trojans: Hidden inside apparently legitimate software for the purpose of going undetected. This blazon of malicious programme can perform any activity it has been programmed to perform on the system [8,9].
Spyware: Like worms, it does not require user intervention to install itself on the organisation and unremarkably works in a hidden way by collecting user or system information in an unauthorized manner [8,9].
Adware: Ordinarily inserted in the system through the installation procedure of other software and its mission is to display unwanted advertising, commonly in the form of pop-upward windows without the user's potency. At present, there is Adware in the grade of browser extensions or plugins.
Ransomware: It is mostly executed from another malware, such as a worm, virus or trojan. Its mission is to completely sequester the system, encrypting all the files and demanding a payment from the user or organization [10,11,12,xiii].
Rootkit: Information technology has the office to access and hide in particularly sensitive areas of the devices it infects, including areas that are not normally accessible to users. Their purpose is to take control of the system and facilitate its remote command while remaining hidden [14,xv].
2.2. Bodily Antivirus Threat Detection and Classification Systems
The principal detection and nomenclature software for this type of malware is the antivirus software, that have evolved in techniques, using mechanisms based on signature, heuristics, rules, and currently the use of bogus intelligence [16,17].
Signature detection [eighteen,19,20] is the traditional method used by antivirus systems and is based on a database generated by the vendor. Any file downloaded to the system is compared to the database and if there is a match, it is malware. The trouble with signature-based detection is that it will but detect those samples that have been previously identified and their signature is stored in the antivirus system database.
To complement signature-based detection and provide a solution to its limitations, heuristic detection techniques were developed [21,22,23]. The performance of heuristic algorithms is based on different criteria, each of them with a score, which determine whether a file is malicious or non. The most mutual iii ways of performing this analysis are [24,25]:
Generic: Compares the actions of a file with another already identified as malicious.
Passive: Analyzes the file individually and tries to decide how it works.
Agile: Runs the sample in a safe environment (sandbox) and determines if its activity is malicious. This strategy is difficult to implement, imposes significant delays, and it can exist avoided by implementing payload activation delays.
Heuristic analysis has two fundamental problems, the start is the large number of faux negatives and the 2nd is the workload on the system. However, information technology improves the ability of antivirus software to detect new samples of malware.
Recently, to increment the capabilities of antivirus systems, the use of auto learning algorithms using artificial intelligence (AI) has been introduced [26,27,28]. The inclusion of these techniques allows for a large-calibration data assay, the identification of patterns and trends, also as the automatic and rapid formulation of predictions. These systems are chosen Endpoint Detection and Response (EDR), also known as Endpoint Thread Detection and Response (ETDR), and implement and endpoint security mechanism [29] at the clients that collects data and sends it to a centralized console for processing, as in a distributed computing surroundings [30]. The data collected is correlated in existent time to find and analyze suspicious activity and processed in a centralized database. Even so, these systems take some weaknesses, as exemplified by G. Karantzas and C. Patsakis [31], for example, the comprehension of the artificial intelligence of the model created or the huge data ingestion required for accurate decision process.
2.3. Obfuscation Techniques
Years ago, a small-scale modification in a piece of malware was able to circumvent antivirus software, so for each virus, we had several versions equally if they were different developments (only transmission assay was able to discover a common origin to assign a suitable virus proper name). However, the development of antivirus software with heuristics and AI, has been very effective in detecting variants of existing malware. The remaining challenge is to detect malware that uses obfuscation techniques, which is the focus of this inquiry.
To avoid detection, several techniques accept been developed. There are diverse techniques currently bachelor to whatever attacker that can be applied individually or in combination to evade the defenses of any organization.
Self-encryption: The use of encryption algorithms or functions that comprise a key included in the body of the malware that allows it to perform the encryption or decryption function in an automated style [32].
Polymorphism: Information technology uses a polymorphic engine to mutate itself and keep its original code intact [33,34,35].
Metamorphism: Information technology can transform itself according to its capabilities to interpret, edit, and rewrite its ain code each fourth dimension it infects a figurer system [36,37].
Armouring: It is programmed to preclude any try at analysis or disassembly, making it impossible to know the original code [38].
Stealth: It completely or partially hides its presence in the system by intercepting requests of the operating organization to interact with infected objects (boot sectors, file arrangement elements, memory, etc.) [39,40].
Covert channels: It uses unauthorized communication channels and manipulates them in an unconventional mode to transmit information undetected past anyone other than the entities operating the covert channel [41,42,43].
These obfuscation techniques make detection process very hard because the antivirus software is not able to read and clarify the code as in the case of any other static file. Moreover, due to the internal randomness of the obfuscation process, information technology is not possible to create signatures of the encrypted code because each sample of the same malware is different. In this paper, we advise to detect such kind of hidden malware by analyzing its beliefs based on the chain of actions executed. Very recently evasion techniques have been applied to ransomware as well to avoid being detected while running. As an example, LockFile [44] performs file encryption by mapping the file to memory to avoid interaction with the hard drive during the process.
ii.iv. Threat Categorization
All adversaries volition always execute a chain of deportment [45,46,47] that are listed in the Cyber Kill Chain [48,49] (run into Effigy 1). This scheme allows to classify attacks into unlike levels of risk and to decide the perspective of the assaulter at each moment. In addition, with the purpose of describing and categorizing antagonist capabilities to better system security, a structured matrix was created with the techniques and tactics used. The matrix known as MITRE ATT&CK (ATT&CK is a pseudonym of ATTACK) includes Tactics, Techniques, and Mutual Adversary Knowledge [fifty] and centralizes this information, allowing organizations to prevent possible threats to their calculator systems.
The unification of these two schemes provides a real agreement of the type of technique and tactics used by an adversary at each stage of the assail process. Past analyzing this information, we can extrapolate models that allow u.s.a. to suggest defensive strategies for detecting the actions of adversaries, and thus mitigate their consequences. Detection and classification systems (antivirus) on the market are very express when performing these tasks in real time on malware that implement obfuscation techniques, because they mostly rely on static file analysis.
For these reasons, nosotros take considered the implementation of a system based on the existent-time analysis of the events [51,52,53] generated in the system and the classification of these events using the MITRE ATT&CK matrix and the Cyber Kill-Concatenation [54]. In this way, nosotros were able to classify each effect in the organization, collecting all the events that have a malicious traceability.
three. Methodology and Implementation
Several Cybersecurity companies dedicate their efforts to the analysis of threats, developing and improving their detection and classification systems. These tasks resulting in the creation of a unique signature, the analysis of its functioning at arrangement and network level, or the study of its source code in depth. As a result, it is possible to obtain an updated knowledge database of known threats to defend reckoner systems. To evade these detection systems, adversaries can apply a multitude of obfuscation techniques, behavior modification and research of unknown techniques. Hence, antivirus companies demand to create new signatures for each variant.
3.1. Related Piece of work
This paper proposes a detection and threat classification system based on events generated past the operating arrangement in real time, classifying them in the MITRE ATT&CK matrix of techniques and tactics together with their corresponding mapping in the Cyber Impale Chain. The criteria applied is based on the analysis of the events generated past dissimilar attacks, checking the tactic and technique where each of them is located within the MITRE ATT&CK matrix and therefore the stage within the Cyber Kill-Concatenation. Although there are existing works that have carried out inquiry on event-based threat detection and classification systems [55,56], the ane proposed is very effective regardless of the obfuscation method employed.
It is important to remark that this system does non pretend to replace the electric current antivirus systems, since they practise their task effectively in nearly of the known cases of malware. However, information technology tin be considered an extension to meliorate antivirus in the case of certain malicious lawmaking that is obfuscated and executed in retention. In most antivirus software, the assay of code is simply triggered by read or write deportment on the difficult bulldoze.
The number of events collected during the execution of suspicious programs can exist very big. Therefore, the current proposal is to friction match those events to the widely recognized MITRE ATT&CK matrix, so allocate as malicious any vector of attack containing techniques and actions considered of loftier-risk (from Execution/Exploitation). In future work, information technology will be possible to provide intelligence to the platform to automatically detect and classify malicious codes more accurately, for instance considering the progression of events. Table 1 shows the list of the 14 MITRE tactics, their correlation with the Cyber Impale Chain, the total number of techniques within each Tactic, and how many of those techniques are considered loftier-risk. Information technology can be observed that for some Tactics, neither technique is considered of high-take chances. For example, the Tactic Discovery has 13 unlike techniques, but none of them is considered malicious. On the other manus, in the case of Command and Control there 8 techniques out of 13 in this category, that are considered loftier-risk. Consequently, events associated with Discovery tactic will non be classified as malicious, while those associated with Command and Control volition very likely classified as malicious (only 5 techniques will not). The reason for having white-listed techniques is considering some techniques, such as command execution, can be used in a legitimate way. For example, arrangement commands tin be executed past any user and practice non stand for any threat.
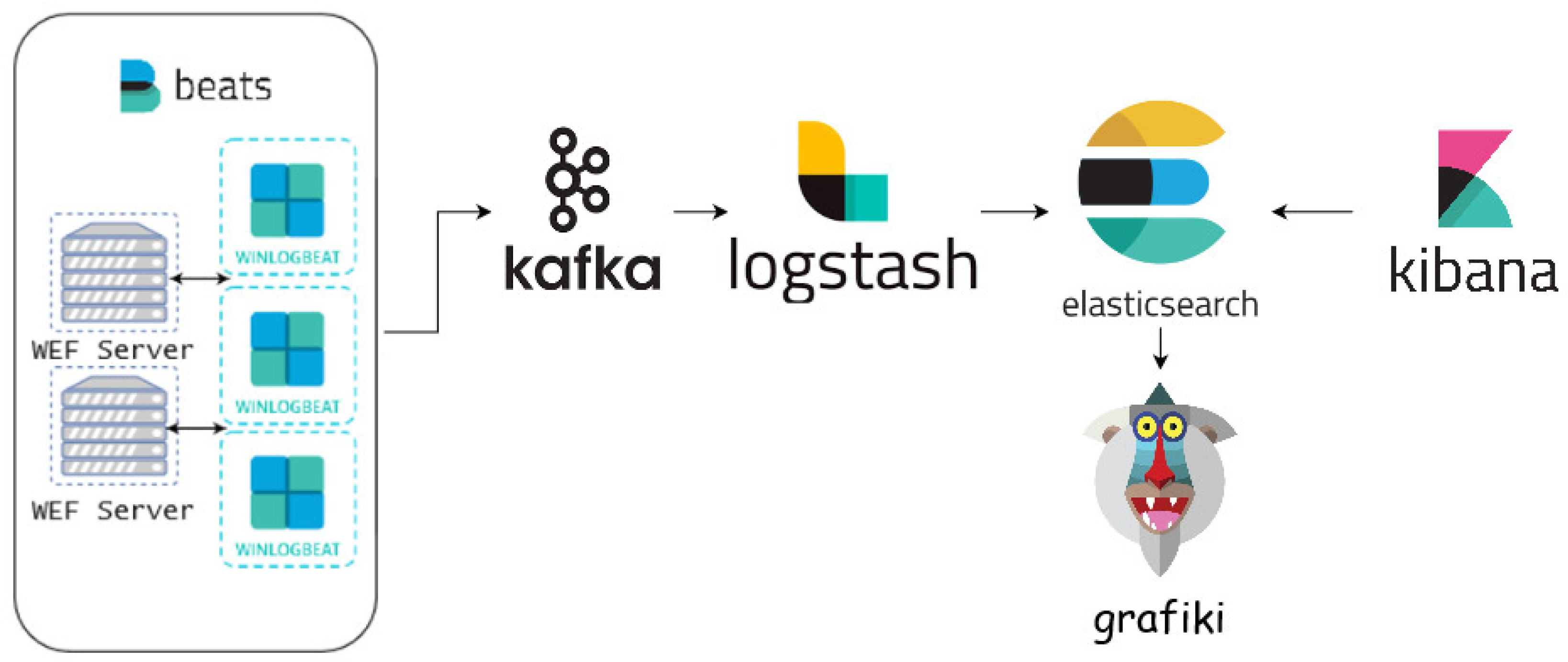
The result-based detection organisation was implemented past combining of a set of open up-source tools to automate the analysis of malicious techniques explained above. Equally a fundamental cadre we used Sysmon [57,58], which runs every bit a resident service on the arrangement and provides logging activity through the Windows upshot log. The advice between systems for sending information uses Winlogbeat [59] which is an open up-source tool for sending Windows event logs to Kafka, which is an open up-source distributed upshot streaming platform. For centralized information reception and analysis, a organisation based on ELK (ElasticSearch, Logstah and Kibana) was also implemented [60]. The first module (Logstah) is a server-side data processing pipeline that ingests multiple sources simultaneously, the second module (ElasticSearch) provides a information search and analytics engine and sends them to the tertiary (Kibana) that facilitates the visualization of the data. Finally, all system information is consumed past Grafiki, which allows the creation of outcome graphs generated during the execution of malicious techniques in the organisation. We have named this detection system EDBS (Event Based Detection Organization). The block diagram of the organization is shown on Figure 2.
The paper published by J. Due north. Praneeth and K. Sreedevi [61] similarly applied some of the proposed tools, but with very limited assay of the results obtained. Just an unspecified piece of software is analyzed against VirusTotal using its hash code. The problem previously discussed can be observed in a similar fashion in other works which implement similar technologies, equally the thesis published by M. Rasool [62] which uses VirusTotal as one of the fundamental components in the nomenclature of malware. In the research published by F. A. Bin Hamid Ali and Yee Yong Len [63], the authors describe a methodology for consequence-driven attack assay based on signatures whereby their classification method only allows them to notice previously known attacks. Other publications, such as the thesis of U. Jain [64], rely on the assay of events generated from the system of the type "Lateral Motility" but does not describe the traceability of the generated events and they are non assigned a chance level. In add-on, there are other publications that implement possible architectures for threat detection and analysis [65,66,67]. These architectures are focused on the detection of suspicious activities in the network, and practice non conceive the utilise of techniques that involve the execution of code directly in the memory of the victim system. Finally, in that location are papers that support the contextualized event-based analysis model, such as the i published by P. Giura and Westward. Wang [68] that describes both a methodology and a framework that can be implemented to perform the detection of different advanced attacks.
iii.2. Implementation and Execution of Experimental Tests
The execution of the tests was performed based on known malicious code and techniques, which commercial antivirus systems already include in their signature databases or detect past means of heuristic algorithms that they have implemented. All of them were executed on a completely updated Microsoft Windows 10 operating system. The description of the malicious codes follows:
Lawmaking A: Powercat.ps1 is a PowerShell script equivalent to the Netcat tool that allows to open up ports, to perform remote connections or exercise port scanning [69].
Lawmaking B: ConPtyShell.ps1 is a PowerShell script that uses the CreatePseudoConsole() function within Windows x version 1809 and allows the execution of a remote command console [70].
Code C: Invoke-PowershellTCP.ps1 is a PowerShell script that is function of the Nishang collection and allows the execution of a remote command console [71].
Code D: MeterpreterTCP.ps1 is a PowerShell version of one of the payloads generated by the Metasploit framework [72], that has a very wide gear up of functionalities and executes in memory, hence offer significant undetectability.
Code E: Mimikatz.ps1 is an open-source application that allows attackers to obtain information on the target organisation, such as stored credentials or Kerberos tickets [73].
Code F: Meterpreter.exe is the executable version of malicious code previously mentioned in "Code D".
In addition, we made use of macros 4.0 (XML) in Excel documents, which are uniform with electric current Microsoft Office systems [74] and correspond one of the techniques currently used to reduce the detection. We also added the use of signed operating system binaries, known every bit LOLBins [75], to carry code execution once the document has been opened.
Code Thousand: The Microsoft Excel document contains a macro 4.0 that runs a local control console using the MSBuild.exe binary.
Lawmaking H: The Microsoft Excel document contains a macro 4.0 that first downloads the file with malicious lawmaking using CertUtil.exe and so executes it using MSBuild.exe, as presented in the previous case.
Similarly, we accept used Visual Basic for Applications (VBA) in Microsoft Office documents. Although these are very well-known, this has allowed us to obtain an approach for the results that nosotros have obtained with our implementation.
Lawmaking I: The Microsoft Word document contains a Visual Basic for Applications (VBA) macro that download and execute a malicious code using PowerShell direct into retention.
In social club to study the current country of the art in obfuscated malware detection, 11 commercial threat detection and nomenclature (antivirus) systems were used. Unlike virtual machines were created with a make clean updated Windows 10 installation and one antivirus at a time.
Afterwards basic initial testing of the aforementioned malware code, three dissimilar obfuscation methods were implemented to perform boosted tests, consisting of encryption using AES algorithms, substitution of office names and known text strings, and encryption using XOR algorithm.
AES (Advanced Encryption Standard) encryption: Information technology is a symmetric block cipher, i.e., information technology operates on groups of bits of fixed length and applies invariant transformations to them. The size of the blocks information technology handles is 128-bits and uses 128, 192, and 256-bit encryption keys.
String substitution: A simple way to evade antivirus systems in some cases is the commutation of known role names with random ones. As a outcome, it is possible to avoid identification by modifying the code signature that is compared with the ane stored in the antivirus system'southward database.
XOR encryption: It is a symmetric encryption based on the XOR logical operator and performs this operation bit past bit.
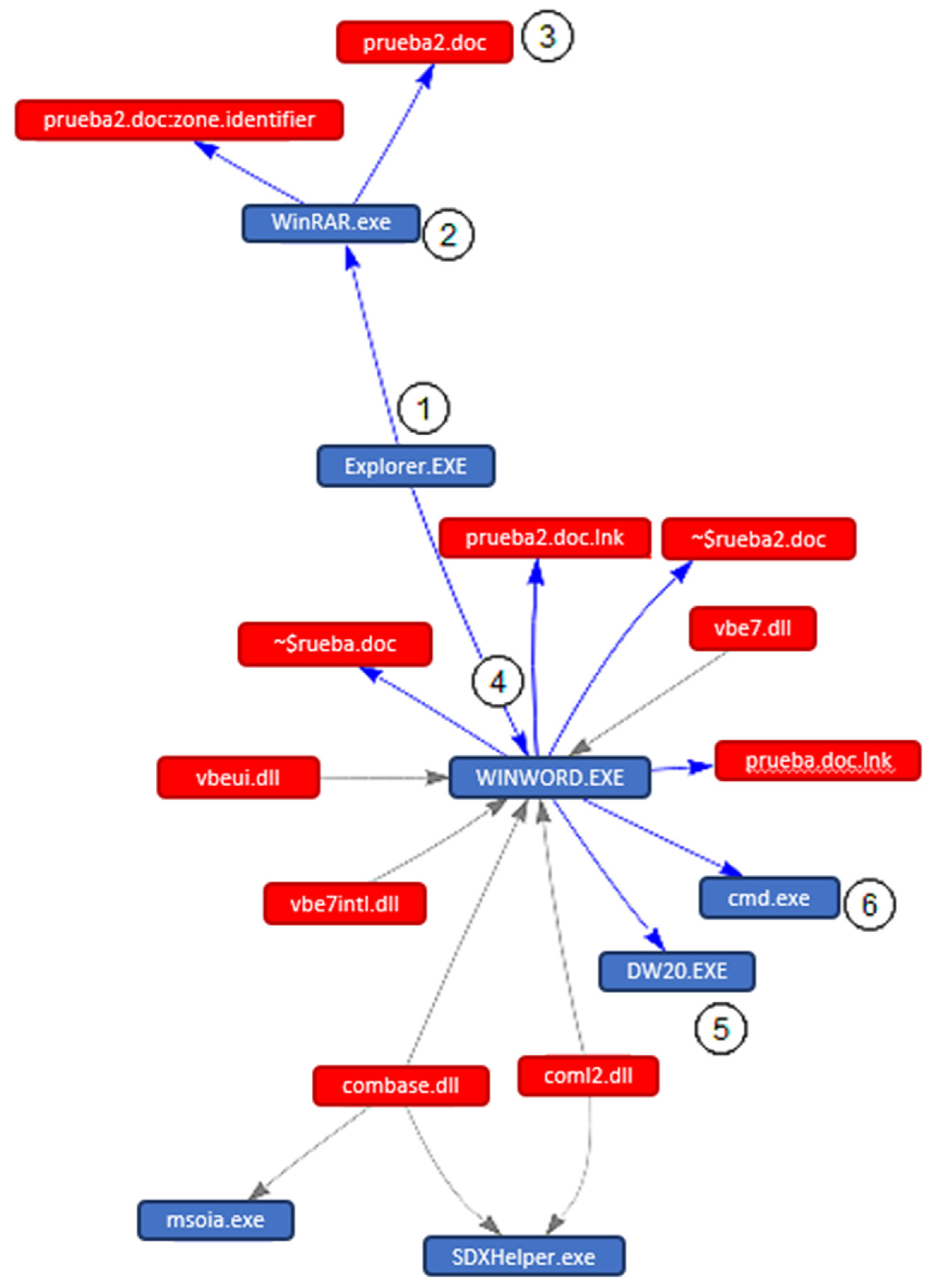
A full general approach of the proposed methodology for data collection and analysis tin be understood following the graph of events shown in Figure 3. This example corresponds to the execution of a Microsoft Word document that has embedded a macro (VBA) [76] with malicious code, that is Code I in the set of tests.
The graph of events shown in Effigy 3, includes all the important events triggered past the execution of Code I. Therefore, the execution process can exist described as follows:
-
The user receives compressed file and proceeds to download it to the system.
-
Launches WinRAR application to obtain the contents of the file.
-
The result of the decompression is the file "test2.doc" ("prueba2.doc" in the graph) which contains the macro with malicious code embedded in it.
-
It is executed past the user and the arrangement calls the WINWORD.exe program to open up the document.
-
When the user enables the execution of the macros an error occurs in the WINWORD.exe binary that calls DW20.exe, which is responsible for compiling an error report.
-
While the previous pace occurs, the macro execution occurs which launches a command console on the arrangement.
The mapping of the steps discussed above onto MITRE ATT&CK, and the Cyber Kill Concatenation are the following:
-
The pace 1 corresponds to the MITRE ATT&CK tactic "Initial Access" and technique "T1566-Phishing" and "Delivery" action in the Cyber Kill Chain.
-
The footstep two corresponds to the MITRE ATT&CK tactic "Execution" and technique "T1204-User Execution" and "Exploitation" activity in the Cyber Kill Chain.
-
The step 3 corresponds to the MITRE ATT&CK tactic "Persistence" and technique "T1137-Office Application Startup" and "Installation" action in the Cyber Impale Concatenation.
-
The step four corresponds to the MITRE ATT&CK tactic "Defense Evasion" and technique "T1055-Process Injection" and "Installation" action in the Cyber Kill Chain.
-
The steps 5 and six corresponds to the MITRE ATT&CK tactic "Execution" and technique "T1059-Command-Line Interface" and "Installation" action in the Cyber Kill Chain.
In this example, the system detects several events that are matched to MITRE ATT&CK and Cyber Kill Concatenation, simply nigh of them are low or medium run a risk. Technique "T1204" in steps 2 and 3 is part of the "Execution" tactic, but it is not considered high-risk, because it means that the user launched the execution of a program such equally Discussion. Similarly, in step 4 the organisation captures a "Defense force Evasion" tactic considering of technique "T1055" which is neither a high-risk technique considering it involves the execution of Dynamic Linked Libraries (DLLs), like almost all windows programs. Conversely, the latest event, besides corresponding to the "Execution" tactic, is the one that really triggers the alert. Technique "T1059" is defined as blazon high-hazard, considering it means that the macro is launching a Control Tool or Ability Beat out for executing whatsoever kind of commands.
One of the features of Microsoft Word, is the ability to create multiple messages automatically out of a list of names and addresses stored in a database. This characteristic is called Mail Merge and tin can be used in conjunction with Open Database Connectivity (ODBC) to connect Word with a database server. It could be very useful to include a macro in that type of documents to verify, using a ping command, if there is connectivity with the database server before attempting to generate mail service letters. Upon opening such document, the arrangement will not trigger any alarm, because information technology contains a benign macro. The sequence of outcome will exist very similar than before, but instead of technique "T1059" at the latest step, the system volition be getting "T1018" (associated with ping command), which is a low-risk Discovery tactic that does not trigger the alarm.
Annotation that the procedure described with the help of the "Lawmaking I" can generalize to other types of attacks that execute in retentiveness for avoiding traditional antivirus detection techniques. The methodology described, may potentially detect whatsoever attack defined by MITRE and will not reveal any risk in the case of benign events.
4. Experimental Results
The proposed methodology was evaluated for dissimilar categories of malware and obfuscation methods. The objective of the experiments is to prove the effectiveness of event collection, the ability to match those events to the MITRE ATT&CK matrix and use that standard to make up one's mind if a threat is present of not. There are unlike attack vectors implemented in our experimental assay that combine dissimilar tactics and techniques from the MITRE ATT&CK matrix. The evaluation is not based on individual malware samples, but on different attack vectors that ultimately implement deportment that trigger system events detected by the proposed architecture. This is a more generalized cess approach that targets non-existing malware or attack techniques and does not attempt to find existing malware, because current antivirus tin can cope with such attacks.
Because of the obfuscation applied, standard antivirus programs are in disadvantage for detecting the malware tested. All the same, the effect-based strategy can detect loftier-take chances events, co-ordinate to the MITRE specification, for the malware. Any assault that triggers high-risk system events is potentially detectable with the proposed arroyo regardless of the obfuscation method implemented by the attacker.
The effect-bases detection organisation helps to perform circuitous analyses, such as experiments using Excel documents with macros four.0, and signed operating system binaries. Lawmaking G and Lawmaking H include malware in the form of Excel macros. Their detail description follows:
Excel-Macro4.0-MSBuild-Cmd (Code K): The execution graph obtained afterwards running Code Yard on the virtual machine is shown in Effigy 4
Corresponding to the image in Figure four, a detailed analysis of the events that have occurred in the arrangement tin can be carried out, which allows for a comprehensive evaluation of the execution process:
-
The user receives an Excel certificate which contains the macros 4.0 that allows malicious execution on the system.
-
Opening the document, the system calls the EXCEL.exe program.
-
Certificate "testapt1.xls" opens, and the user enables the execution of macros embedded in the certificate.
-
Excel calls the binary MSBuild.exe that executes the commands in the arrangement.
-
As a result, command prompt is opened on the organization.
The mapping of the steps described higher up onto MITRE ATT&CK and the Cyber Kill Chain is the post-obit:
-
The footstep 1 corresponds to the MITRE ATT&CK tactic "Initial Access" and technique "T1566-Phishing" and "Delivery" action in the Cyber Impale Chain.
-
The step ii corresponds to the MITRE ATT&CK tactic "Execution" and technique "T1204-User Execution" and "Exploitation" action in the Cyber Kill Concatenation.
-
The footstep 3 corresponds to the MITRE ATT&CK tactic "Persistence" and technique "T1137-Office Application Startup" and "Installation" action in the Cyber Kill Concatenation.
-
The step 4 corresponds to the MITRE ATT&CK tactic "Defense Evasion" and technique "T1127-Trusted Programmer Utilities Proxy Execution" and "Installation" action in the Cyber Kill Chain.
-
The stride 5 corresponds to the MITRE ATT&CK tactic "Execution" and technique "T1059-Command-Line Interface" and "Exploitation" action in the Cyber Kill Concatenation.
Excel-Macro4.0-CertUtil-MSBuild-RevShell (Code H): The execution graph obtained after running this test is detailed in Figure 5:
The post-obit points item the execution procedure, which allows for a detailed assay of the events that accept occurred in the system.
-
The user receives an Excel document containing macros 4.0 which allow malicious execution on the system.
-
When the user proceeds to open up the document, the system calls the EXCEL.exe program.
-
The certificate "testapt2.xls" is opened and the user enables the execution of macros.
-
The binary CertUtil.exe is executed at the beginning, which downloads the file with the malicious commands to the system.
-
The file "readme2.txt" containing the malicious lawmaking is stored in a path on the computer.
-
Later on, the binary MSBuild.exe is launched and it runs the contents of the file, in this case it contains C# lawmaking that executes PowerShell commands.
-
It is possible to observe how "microsoft.powershell.commands.management" is executed.
-
Policy compliance tests are carried out and too detected as events (8a, 8b), although they are not classified equally take chances events.
The mapping of the steps described above onto MITRE ATT&CK and the Cyber Kill Chain is the following:
-
The step 1 corresponds to the MITRE ATT&CK tactic "Initial Access" and technique "T1566-Phishing" and "Delivery" action in the Cyber Kill Chain.
-
The pace two corresponds to the MITRE ATT&CK tactic "Execution" and technique "T1204-User Execution" and "Exploitation" action in the Cyber Impale Concatenation.
-
The step three corresponds to the MITRE ATT&CK tactic "Persistence" and technique "T1137-Office Application Startup" and "Installation" activeness in the Cyber Kill Chain.
-
The steps 4 and 5 correspond to the MITRE ATT&CK tactic "Defence force Evasion" and technique "T1292-Indirect Command Execution" and "Installation" action in the Cyber Kill Chain.
-
The step 6 corresponds to the MITRE ATT&CK tactic "Defense Evasion" and technique "T1127-Trusted Developer Utilities Proxy Execution" and "Installation" action in the Cyber Impale Chain.
-
The step seven corresponds to the MITRE ATT&CK tactic "Execution" and technique "T1059-Command and Scripting Interpreter" and "Exploitation" action in the Cyber Kill Concatenation.
The Event-based detection arrangement (EBDS) proposed is able notice all malicious activity, considering the malware ever triggers an event classified every bit high-risk by MITRE. Fifty-fifty in the case of using obfuscation methods, EBDS tin can detect the set on once the original code is restored and key components (such as PowerShell) are executed. On the other hand, static assay of the malicious file is not able to detect the key components considering the payload is encrypted.
The comparison between the performance of different antivirus software, using techniques such as obfuscation and extracting malicious payloads in-memory, is shown in the post-obit tables. Table ii, without obfuscation, shows that well-nigh malware codes are detected past several commercial antivirus packages. However, later applying dissimilar obfuscation methods, detection is much harder (Table 3, Table 4 and Table v).
It is also important to mention that about antivirus are giving an alarm considering they detect the obfuscation technique, giving a warning of "suspicious file", only not detecting the malware itself. Every bit an instance, lawmaking B is not detected past BitDefender without obfuscation (Table i), but information technology is detected when using AES encryption (Table 2), clearly considering the utilize of encryption tools is raising the flag, since the payload cannot be read until executed. This detection strategy typically yields false positives if the user works with legitimate encrypted or coded files. We were able to prove such beliefs past creating a harmless PowerShell lawmaking to just display a "hello world" bulletin and obfuscating the file using AES; this file was also detected as malicious past several antivirus programs. The file was uploaded to VirusTotal [77,78] on 18 May 2021, and it was labeled as malicious by 9 antivirus programs.
v. Discussion
Traditional systems for detection and nomenclature of threats in networks and computer systems are increasingly encountering difficulties for early detection of malicious lawmaking. This is because detection systems based on signature and heuristics accept become outdated in the battle against novel evasion techniques. Therefore, this paper highlights the importance of implementing culling detection methods, such every bit those based on the analysis and classification of events generated within the user's calculator. Through this type of analysis, information technology is possible to detect avant-garde techniques and establish security checkpoints for events generated in the system that may bespeak that the system is existence compromised.
The results presented in this paper correspond to commercial antivirus software and the proposed Upshot Management System EBDS, all running locally in the stop-user estimator. In big companies, information technology is possible to use SIEM (Security Information and Consequence Direction) systems or corporate versions of antivirus software that centralize events, therefore attaining better results than a stand up-alone antivirus. Nonetheless, the work presented hither was carried out with the focus on abode, habitation-office, or small businesses, which demand to rely on local estimator detection.
The results show that, by applying obfuscation techniques, it is possible to hibernate malicious code from any detection system based on lawmaking signatures. Any encrypted code (malicious or benign) uploaded to VirusTotal will yield "safe" results, or peradventure a warning related to fact that the file is encrypted. In add-on, nigh advanced attacks manage to excerpt the obfuscated malicious code directly in the memory, without additional hard bulldoze access, therefore fugitive a possible signature-based detection, considering antivirus softwares scan files only while reading or writing to the hard drive.
Obfuscation techniques take no limits, at that place are multiple techniques and combination of techniques that tin can be practical. Since these techniques use a randomly generated key, every sample of obfuscated malware is different, and the creation of a general file signature is not possible. In improver, completely new malware, even without obfuscation, cannot exist detected through signatures.
6. Conclusions
We have presented a detection system based on open up-source tools, which is able to capture security critical events of the system. The proposed event-based analysis method, linked to MITRE Cyber Impale Concatenation, tin can end the set on at the correct moment, when reaching the land of "Execution/Exploitation", preventing that PowerShell or Cmd are called.
Although standard antivirus programs are very constructive and computationally efficient while detecting malware in full general, they struggle with different obfuscation techniques. When obfuscation is applied to the malware, the proposed event-based strategy offers a second layer of assay to better detection rates compared to the fix of non-detections and false positives of traditional antivirus systems alone.
For the purpose of experimentally validating the methodology proposed in this article, a comparative study has been carried out against ten traditional detection systems (antivirus), ever using the same set of samples and with the same obfuscation method in each case. Antivirus software was tested in different Windows 10 virtual machines, allowing the software to use all the potential of heuristics and real-time detection modules; notwithstanding, it did not perform well for samples with obfuscation. On the other mitt, the proposed methodology was able to detect the detect the sequence of events that were escalating in the severity.
As future work, Artificial Intelligence algorithms will be added to find hazardous sequences of events, potentially being able to detect threats even in before stages of the assail. The current detection method was implemented by finding the state of "Execution/Exploitation", only without exploiting details about sequences of states.
Author Contributions
Conceptualization, A.P.-S.; methodology, A.P.-S. and R.P.; software, A.P.-S.; validation, A.P.-S. and R.P.; investigation, A.P.-S. and R.P.; writing—original draft preparation, A.P.-S. and R.P.; writing—review and editing, A.P.-S. and R.P. All authors accept read and agreed to the published version of the manuscript.
Funding
This research no received external funding.
Institutional Review Board Statement
Not applicative.
Informed Consent Statement
Not applicable.
Data Availability Statement
Non applicable.
Conflicts of Interest
The authors declare no disharmonize of interest.
References
- Botacin, M.; Ceschin, F.; de Geus, P.; Grégio, A. Nosotros need to talk about antiviruses: Challenges & pitfalls of AV evaluations. Comput. Secur. 2020, 95, 101859. [Google Scholar] [CrossRef]
- Robert, J.-One thousand.; Chen, T. The Development of Viruses and Worms. In Statistical Methods in Computer Security; CRC Press: Boca Raton, FL, The states, 2004; pp. 265–285. [Google Scholar]
- Namanya, A.P.; Cullen, A.; Awan, I.U.; Disso, J.P. The Earth of Malware: An Overview. In Proceedings of the 2018 IEEE 6th International Conference on Future Internet of Things and Cloud (FiCloud), Barcelona, Espana, 6–eight Baronial 2018; pp. 420–427. [Google Scholar]
- Zuo, Z.; Zhu, Q.; Zhou, One thousand. Infection, imitation and a hierarchy of calculator viruses. Comput. Secur. 2006, 25, 469–473. [Google Scholar] [CrossRef]
- Schneider, W. Computer viruses: What they are, how they work, how they might go you, and how to control them in academic institutions. Behav. Res. Methods Instrum. Comput. 1989, 21, 334–340. [Google Scholar] [CrossRef]
- Choi, Y.-H.; Li, L.; Liu, P.; Kesidis, G. Worm virulence estimation for the containment of local worm outbreak. Comput. Secur. 2010, 29, 104–123. [Google Scholar] [CrossRef]
- Zhou, H.; Hu, Y.; Yang, X.; Pan, H.; Guo, W.; Zou, C.C. A Worm Detection System Based on Deep Learning. IEEE Access 2020, 8, 205444–205454. [Google Scholar] [CrossRef]
- Gezer, A.; Warner, One thousand.; Wilson, C.; Shrestha, P. A flow-based arroyo for Trickbot banking trojan detection. Comput. Secur. 2019, 84, 179–192. [Google Scholar] [CrossRef]
- Dong, C.; Liu, Y.; Chen, J.; Liu, X.; Guo, West.; Chen, Y. An Unsupervised Detection Approach for Hardware Trojans. IEEE Access 2020, viii, 158169–158183. [Google Scholar] [CrossRef]
- Meland, P.H.; Bayoumy, Y.F.F.; Sindre, M. The Ransomware-every bit-a-Service economy inside the darknet. Comput. Secur. 2020, 92, 101762. [Google Scholar] [CrossRef]
- Liu, West. Modeling Ransomware Spreading by a Dynamic Node-Level Method. IEEE Access 2019, 7, 142224–142232. [Google Scholar] [CrossRef]
- Hampton, N.; Baig, Z.; Zeadally, S. Ransomware behavioural analysis on windows platforms. J. Inf. Secur. Appl. 2018, forty, 44–51. [Google Scholar] [CrossRef]
- Lee, South.-J.; Shim, H.-Y.; Lee, Y.-R.; Park, T.-R.; Park, S.-H.; Lee, I.-G. Study on Systematic Ransomware Detection Techniques. In Proceedings of the 2021 23rd International Conference on Avant-garde Communication Technology (ICACT), Online, 7–10 February 2021; pp. 297–301. [Google Scholar]
- Baliga, A.; Iftode, L.; Chen, X. Automated containment of rootkits attacks. Comput. Secur. 2008, 27, 323–334. [Google Scholar] [CrossRef]
- Tian, D.; Ma, R.; Jia, X.; Hu, C. A Kernel Rootkit Detection Approach Based on Virtualization and Machine Learning. IEEE Admission 2019, 7, 91657–91666. [Google Scholar] [CrossRef]
- Rad, B.B.; Masrom, Yard.; Ibrahim, Southward. Evolution of Computer Virus Concealment and Anti-Virus Techniques: A Short Survey. April 2011. Available online: http://arxiv.org/abs/1104.1070 (accessed on 21 Nov 2021).
- Bhaskar, Five.; Patil, R.J.J. Estimator Virus and Antivirus Software—A Cursory Review. Int. J. Adv. Manag. Econ. 2014, 4, 4. [Google Scholar]
- Al-Asli, G.; Ghaleb, T.A. Review of Signature-based Techniques in Antivirus Products. In Proceedings of the 2019 International Briefing on Computer and Information Sciences (ICCIS), Aljouf, Saudi Arabi, 3–four April 2019; pp. 1–six. [Google Scholar]
- Scott, J. Signature Based Malware Detection Is Dead. February 2017. Bachelor online: https://icitech.org/wp-content/uploads/2017/02/ICIT-Analysis-Signature-Based-Malware-Detection-is-Dead.pdf (accessed on nine September 2021).
- Sathyanarayan, V.Southward.; Kohli, P.; Bruhadeshwar, B. Signature Generation and Detection of Malware Families. In Information Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2008; pp. 336–349. [Google Scholar]
- Bazrafshan, Z.; Hashemi, H.; Fard, S.M.H.; Hamzeh, A. A survey on heuristic malware detection techniques. In Proceedings of the The 5th Conference on Information and Knowledge Applied science, Tehran, Iran, 28–30 May 2013; pp. 113–120. [Google Scholar]
- Treadwell, Due south.; Zhou, Grand. A heuristic approach for detection of obfuscated malware. In Proceedings of the 2009 IEEE International Conference on Intelligence and Security Computer science, Dallas, TX, USA, 8–11 June 2009; pp. 291–299. [Google Scholar]
- Harley, D.; Lee, A. Heuristic Analysis–Detecting Unknown Viruses 2007. Available online: https://world wide web.welivesecurity.com/wp-content/uploads/200x/white-papers/Heuristic_Analysis.pdf (accessed on 10 October 2021).
- Dube, T.; Raines, R.; Peterson, Thou.; Bauer, K.; Grimaila, M.; Rogers, S. Malware target recognition via static heuristics. Comput. Secur. 2012, 31, 137–147. [Google Scholar] [CrossRef]
- Aslan, O.; Samet, R. A Comprehensive Review on Malware Detection Approaches. IEEE Admission 2020, 8, 6249–6271. [Google Scholar] [CrossRef]
- Wang, X.; Yang, Thou.; Li, Y.; Liu, D. Review on the application of bogus intelligence in antivirus detection systemi. In Proceedings of the 2008 IEEE Conference on Cybernetics and Intelligent Systems, Chengdu, China, 21–24 September 2008; pp. 506–509. [Google Scholar]
- Singhal, P. Malware Detection Module using Machine Learning Algorithms to Assist in Centralized Security in Enterprise Networks. Int. J. Netw. Secur. Its Appl. 2012, iv, 61–67. [Google Scholar] [CrossRef]
- De Lima, S.Yard.L.; de Silva, H.One thousand.Fifty.; da Luz, J.H.S.; exercise Lima, H.J.N.; de Silva, Due south.50.P.; de Andrade, A.B.A.; da Silva, A.1000. Artificial intelligence-based antivirus in order to detect malware preventively. Prog. Artif. Intell. 2020. [Google Scholar] [CrossRef]
- Forain, I.; de Oliveira Albuquerque, R.; Sandoval Orozco, A.; García Villalba, Fifty.; Kim, T.-H. Endpoint Security in Networks: An OpenMP Approach for Increasing Malware Detection Speed. Symmetry 2017, nine, 172. [Google Scholar] [CrossRef]
- Latorre, J.M.; Cerisola, S.; Ramos, A.; Palacios, R. Analysis of stochastic trouble decomposition algorithms in computational grids. Ann. Oper. Res. 2009, 166. [Google Scholar] [CrossRef]
- Karantzas, G.; Patsakis, C. An Empirical Cess of Endpoint Detection and Response Systems against Advanced Persistent Threats Assault Vectors. J. Cybersecur. Priv. 2021, i, 387–421. [Google Scholar] [CrossRef]
- Galteland, H.; Gjøsteen, K. Malware, Encryption, and Rerandomization–Everything Is Under Attack. In Proceedings of the International Briefing on Cryptology, Kuala Lumpur, Malaysia, 1–two December 2017; pp. 233–251. [Google Scholar]
- Kong, D.; Jhi, Y.-C.; Gong, T.; Zhu, S.; Liu, P.; Xi, H. SAS: Semantics aware signature generation for polymorphic worm detection. Int. J. Inf. Secur. 2011, x, 269–283. [Google Scholar] [CrossRef]
- Wanswett, B.; Kalita, H.Grand. The Threat of Obfuscated Zero Day Polymorphic Malwares: An Analysis. In Proceedings of the 2015 International Briefing on Computational Intelligence and Communication Networks (CICN), Jabalpur, Republic of india, 12–fourteen December 2015; pp. 1188–1193. [Google Scholar]
- Tang, Y.; Xiao, B.; Lu, Ten. Using a bioinformatics approach to generate accurate exploit-based signatures for polymorphic worms. Comput. Secur. 2009, 28, 827–842. [Google Scholar] [CrossRef]
- Daoud, E. Al Metamorphic Viruses Detection Using Bogus Allowed Organization. In Proceedings of the 2009 International Conference on Communication Software and Networks, Chengdu, Prc, 27–28 February 2009; pp. 168–172. [Google Scholar]
- Gibert, D.; Mateu, C.; Planes, J.; Marques-Silva, J. Auditing static machine learning anti-Malware tools against metamorphic attacks. Comput. Secur. 2021, 102, 102159. [Google Scholar] [CrossRef]
- Filiol, E. Stiff Cryptography Armoured Figurer Viruses Forbidding Code Analysis: The Bradley Virus. Ph.D. Thesis, Institut National de Recherche en Informatique et en Automatique, Le Chesnay-Rocquencourt, France, 2004. [Google Scholar]
- Rudd, E.Thousand.; Rozsa, A.; Gunther, M.; Boult, T.E. A Survey of Stealth Malware Attacks, Mitigation Measures, and Steps Toward Autonomous Open World Solutions. IEEE Commun. Surv. Tutor. 2017, 19, 1145–1172. [Google Scholar] [CrossRef]
- Maiorca, D.; Ariu, D.; Corona, I.; Aresu, G.; Giacinto, G. Stealth attacks: An extended insight into the obfuscation effects on Android malware. Comput. Secur. 2015, 51, sixteen–31. [Google Scholar] [CrossRef]
- Patsakis, C.; Casino, F.; Katos, V. Encrypted and covert DNS queries for botnets: Challenges and countermeasures. Comput. Secur. 2020, 88, 101614. [Google Scholar] [CrossRef]
- Nadler, A.; Aminov, A.; Shabtai, A. Detection of malicious and low throughput data exfiltration over the DNS protocol. Comput. Secur. 2019, fourscore, 36–53. [Google Scholar] [CrossRef]
- Ho, J.-W. Covert Channel Establishment Through the Dynamic Adaptation of the Sequential Probability Ratio Exam to Sensor Data in IoT. IEEE Access 2019, 7, 146093–146107. [Google Scholar] [CrossRef]
- Loman, Yard. LockFile Ransomware's Box of Tricks: Intermittent Encryption and Evasion–Sophos News. 2021. Available online: https://news.sophos.com/en-the states/2021/08/27/lockfile-ransomwares-box-of-tricks-intermittent-encryption-and-evasion/ (accessed on 31 August 2021).
- Chen, P.; Desmet, L.; Huygens, C. A Study on Advanced Persistent Threats. In Proceedings of the IFIP International Conference on Communications and Multimedia Security, Aveiro, Portugal, 25–26 September 2014; pp. 63–72. [Google Scholar]
- Ahmad, A.; Webb, J.; Desouza, K.C.; Boorman, J. Strategically-motivated advanced persistent threat: Definition, procedure, tactics and a disinformation model of counterattack. Comput. Secur. 2019, 86, 402–418. [Google Scholar] [CrossRef]
- Virvilis, Northward.; Gritzalis, D.; Apostolopoulos, T. Trusted Calculating vs. Avant-garde Persistent Threats: Tin a Defender Win This Game? In Proceedings of the 2013 IEEE 10th International Conference on Ubiquitous Intelligence and Computing and 2013 IEEE 10th International Conference on Autonomic and Trusted Computing, Vietri sul Mare, Italia, 18–21 Dec 2013; pp. 396–403. [Google Scholar]
- Yadav, T.; Rao, A.M. Technical Aspects of Cyber Kill Chain. In Proceedings of theThird International Symposium on Security in Computing and Communications (SSCC'fifteen), Kochi, India, ten–thirteen August 2015; pp. 438–452. [Google Scholar]
- Bahrami, P.North.; Dehghantanha, A.; Dargahi, T.; Parizi, R.Thousand.; Raymond Choo, K.-K.; Javadi, H.H.S. Cyber Kill Concatenation-Based Taxonomy of Avant-garde Persistent Threat Actors: Analogy of Tactics, Techniques, and Procedures. J. Inf. Procedure. Syst. 2019, 15, 865–889. [Google Scholar] [CrossRef]
- Al-Shaer, R.; Spring, J.M.; Christou, E. Learning the Associations of MITRE ATT&CK Adversarial Techniques. Apr 2020. Available online: http://arxiv.org/abs/2005.01654 (accessed on 21 December 2021).
- Alexandru, Chiliad. Automation of Log Analysis Using the Hunting ELK Stack. Rom. Cyber Secur. J. 2021, 3, 59–64. [Google Scholar]
- Al Shibani, Grand.; Anupriya, Eastward. Automatic Threat Hunting Using ELK Stack-A Case Study. Indian J. Comput. Sci. Eng. 2019, ten, 118–127. [Google Scholar] [CrossRef]
- Kebande, V.R.; Karie, N.M.; Ikuesan, R.A. Existent-fourth dimension monitoring every bit a supplementary security component of vigilantism in modern network environments. Int. J. Inf. Technol. 2021, 13, 5–17. [Google Scholar] [CrossRef]
- Kim, H.; Kwon, H.; Kim, K.Yard. Modified cyber kill chain model for multimedia service environments. Multimed. Tools Appl. 2019, 78, 3153–3170. [Google Scholar] [CrossRef]
- Sapegin, A.; Jaeger, D.; Cheng, F.; Meinel, C. Towards a system for complex analysis of security events in large-scale networks. Comput. Secur. 2017, 67, 16–34. [Google Scholar] [CrossRef]
- Tsigkritis, T.; Spanoudakis, Thou. Assessing the genuineness of events in runtime monitoring of cyber systems. Comput. Secur. 2013, 38, 76–96. [Google Scholar] [CrossRef]
- Mavroeidis, V.; Jøsang, A. Data-Driven Threat Hunting Using Sysmon. In Proceedings of the 2nd International Conference on Cryptography, Security and Privacy, Guiyang, China, 16–nineteen March 2018; ACM: New York, NY, Usa, 2018; pp. 82–88. [Google Scholar]
- Microsoft Sysmon. 1996. Available online: https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon (accessed on 18 Dec 2021).
- Elastic Winlogbeat. 2018. Available online: https://world wide web.elastic.co/es/downloads/beats/winlogbeat (accessed on 18 December 2021).
- Elastic Elasticsearch, Logstash, Kibana (ELK). 2010. Available online: https://www.elastic.co/es/what-is/elk-stack (accessed on 18 December 2021).
- Pranneth, J.Northward.; Sreedevi, M. Detecting and Analyzing the Malicious Windows Events using Winlogbeat and ELK Stack. Int. J. Recent Technol. Eng. 2019, vii, 716–720. [Google Scholar]
- Fatemi, One thousand.R.; Ghorbani, A.A. Threat Hunting in Windows Using Big Security Log Data. In Security, Privacy and Forensics Issues in Big Data; IGI Global: Hershey, PA, Usa, 2020; pp. 168–188. [Google Scholar] [CrossRef]
- Bin Hamid Ali, F.A.; Len, Y.Y. Development of host based intrusion detection system for log files. In Proceedings of the 2011 IEEE Symposium on Concern, Engineering and Industrial Applications (ISBEIA), Langkawi, Malaysia, 25–28 September 2011; pp. 281–285. [Google Scholar]
- Jain, U. Lateral Motion Detection Using ELK Stack. Master's Thesis, Academy of Houston, Houston, TX, USA, 2018. [Google Scholar]
- Yang, Chiliad.; Cai, L.; Yu, A.; Meng, D. A Full general and Expandable Insider Threat Detection Arrangement Using Baseline Bibelot Detection and Scenario-Driven Alarm Filters. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Calculating And Communications/12th IEEE International Conference On Big Information Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–iii August 2018; pp. 763–773. [Google Scholar]
- Torkaman, A.; Bahrololum, One thousand.; Tadayon, M.H. A threat-aware Host Intrusion Detection System architecture model. In Proceedings of the 7'th International Symposium on Telecommunication (IST'2014), Tehran, Iran, 9–11 September 2014; IEEE: Piscataway, NJ, USA; pp. 929–933. [Google Scholar]
- Abubakar, A.; Pranggono, B. Machine learning based intrusion detection arrangement for software defined networks. In Proceedings of the 2017 7th International Conference on Emerging Security Technologies (EST), Canterbury, UK, 6–8 September 2017; pp. 138–143. [Google Scholar]
- Giura, P.; Wang, W. A Context-Based Detection Framework for Avant-garde Persistent Threats. In Proceedings of the 2012 International Briefing on Cyber Security, Alexandria, VA, USA, 14–xvi December 2012; IEEE: Piscataway, NJ, USA; pp. 69–74. [Google Scholar]
- Douglas, K. Powercat. 2015. Available online: https://www.sans.org/reading-room/whitepapers/testing/powercat-35807 (accessed on 23 November 2021).
- Cocomazzi, A. ConPtyShell. Github Repository. 2019. Available online: https://github.com/antonioCoco/ConPtyShell (accessed on 23 November 2021).
- Mittal, Due north. Invoke-PowerShellTcp. Github Repository. 2015. Bachelor online: https://github.com/samratashok/nishang/tree/chief/Shells (accessed on 23 November 2021).
- More, H. Metasploit Framework. 2003. Available online: https://www.metasploit.com/ (accessed on 21 October 2021).
- Delpy, B. Mimikatz. Github Repository. 2014. Available online: https://github.com/gentilkiwi/mimikatz. (accessed on 23 Dec 2021).
- Bontchev, V. The bug of wordmacro virus upconversion. Comput. Secur. 1999, eighteen, 241–255. [Google Scholar] [CrossRef]
- Oddvar, 1000.; Somerville, Fifty. Living off the State Binaries and Scripts (and also Libraries). Github Repository. 2018. Available online: https://lolbas-project.github.io/# (accessed on 23 December 2021).
- Makris, C. Evaluation of the Detection Capabilities of the Open Source SIEM HELK. Primary'due south Thesis, University of Piraeus, Piraeus, Greece, 2020. [Google Scholar]
- Hsu, F.-H.; Lee, C.-H.; Luo, T.; Chang, T.-C.; Wu, M.-H. A Deject-Based Real-Fourth dimension Mechanism to Protect End Hosts against Malware. Appl. Sci. 2019, nine, 3748. [Google Scholar] [CrossRef]
- Peng, P.; Yang, L.; Song, L.; Wang, Thou. Opening the Blackbox of VirusTotal. In Proceedings of the Cyberspace Measurement Briefing, Amsterdam, The Netherlands, 21–23 October 2019; ACM: New York, NY, United states of america, 2019; pp. 478–485. [Google Scholar]
Figure one. Cyber Kill Chain and MITRE ATT&CK.
Figure 1. Cyber Kill Chain and MITRE ATT&CK.
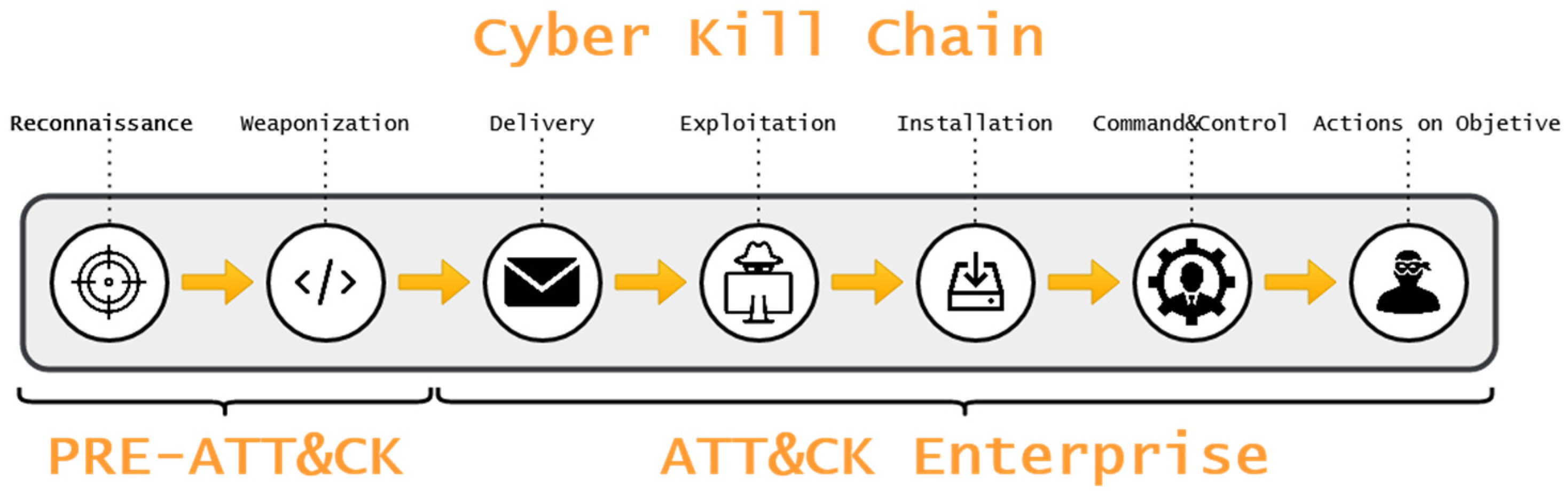
Figure 2. Result Based Detection Arrangement (EBDS) Diagram.
Figure ii. Consequence Based Detection Organization (EBDS) Diagram.
Effigy 3. Upshot of malicious macro execution in a Microsoft Give-and-take document.
Figure three. Effect of malicious macro execution in a Microsoft Word document.
Effigy 4. Result of the execution of an Excel document with MSBuild.exe.
Figure 4. Result of the execution of an Excel document with MSBuild.exe.
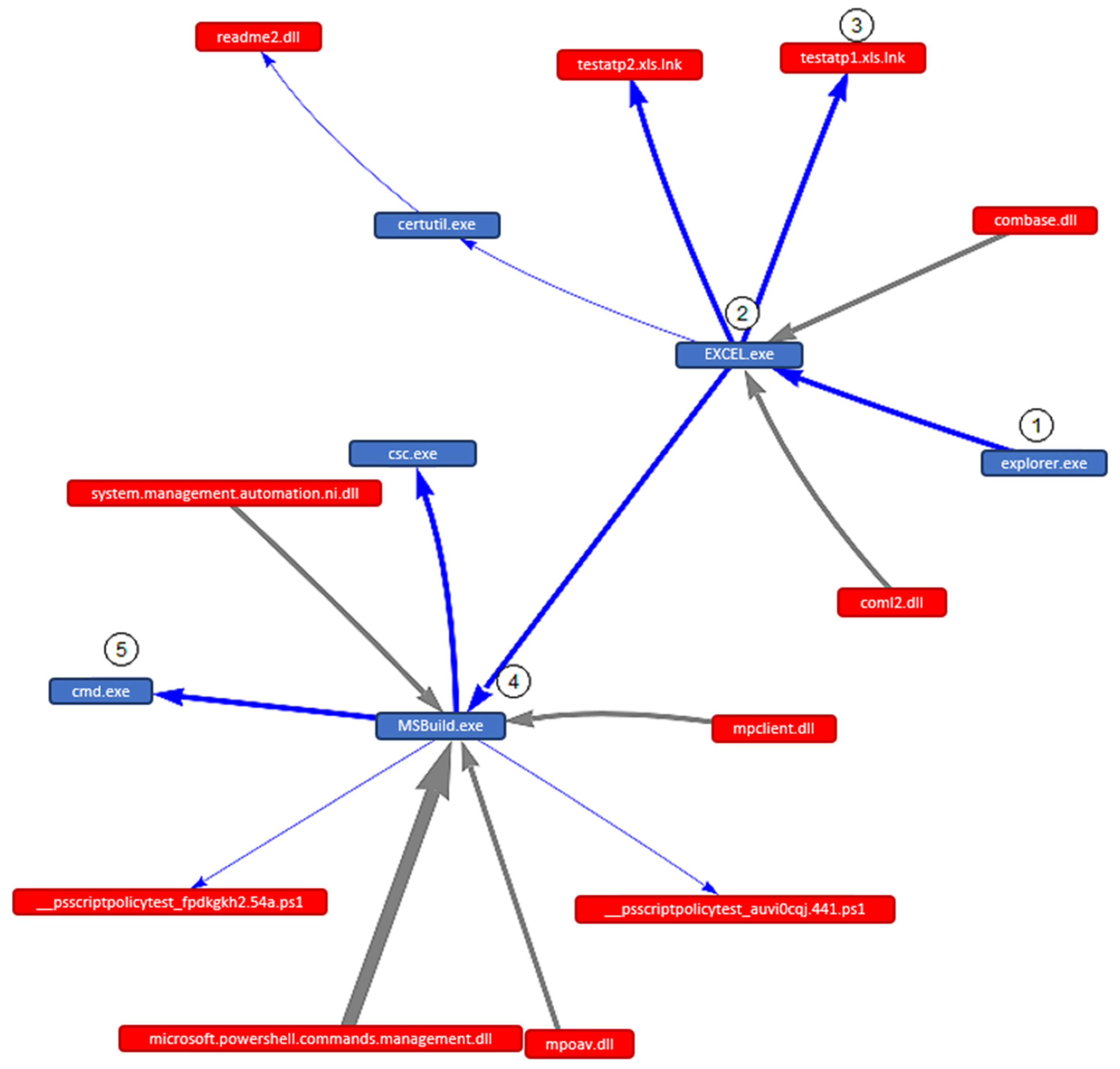
Figure five. Result of Excel document execution with CertUtil.exe and MSBuild.exe.
Figure 5. Consequence of Excel document execution with CertUtil.exe and MSBuild.exe.
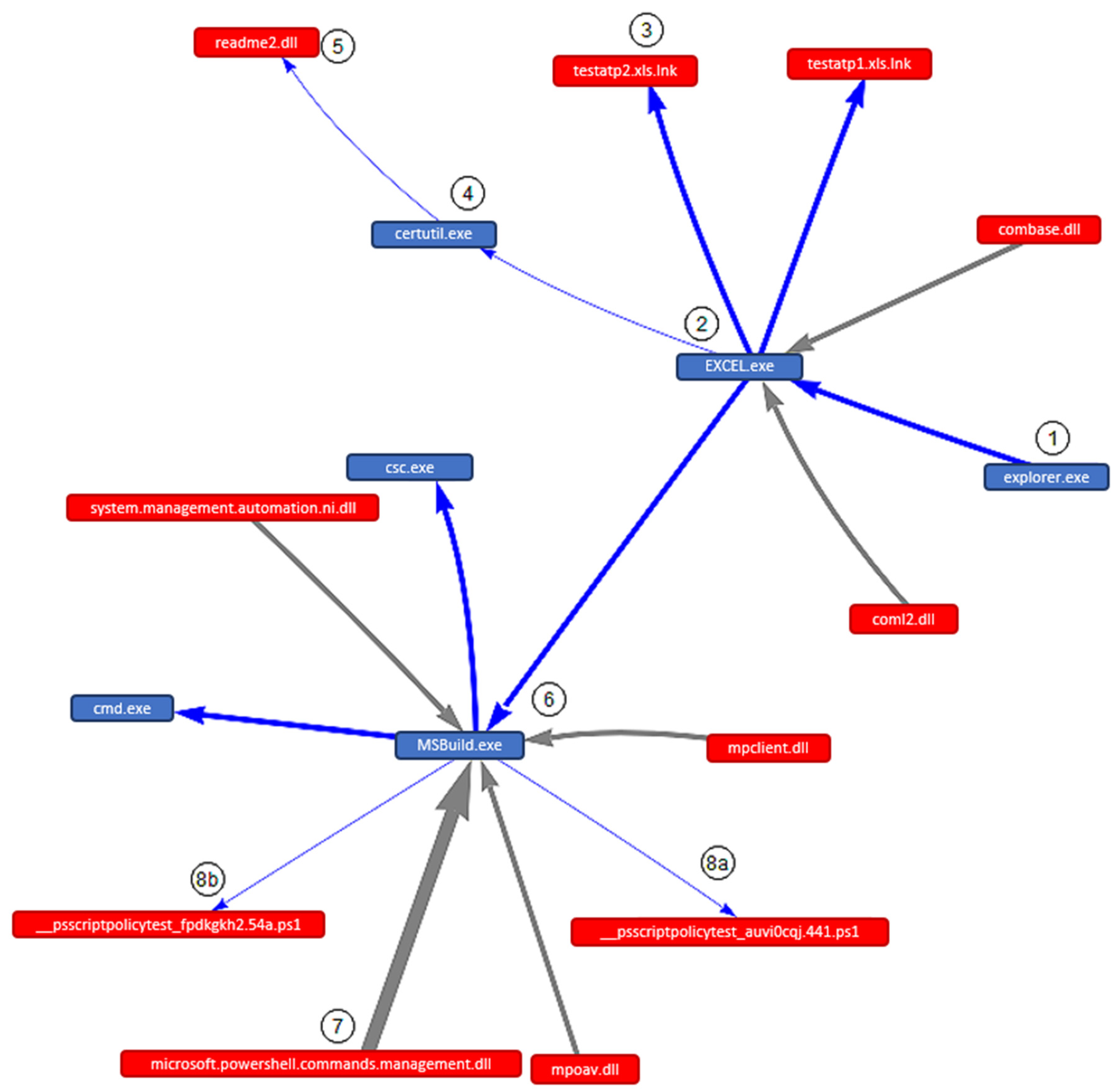
Table ane. Classification method using MITRE ATT&CK matrix and Cyber Kill Chain.
Table i. Classification method using MITRE ATT&CK matrix and Cyber Kill Chain.
| MITRE ATT&CK Tactics | Cyber Kill Chain | Number of High-Risk Techniques | Classified as Malicious |
|---|---|---|---|
| Reconnaissance | Reconnaissance | 0/10 | ✕ |
| Resource Evolution | Weaponization | 0/7 | ✕ |
| Initial Access | Delivery | 0/nine | ✕ |
| Execution | Exploitation | 5/10 | ✓ |
| Persistence | Installation | iii/nine | ✓ |
| Privilege Escalation | Actions on Objectives | 4/x | ✓ |
| Defense force Evasion | Installation | 10/27 | ✓ |
| Credential Access | Deportment on Objectives | 3/seven | ✓ |
| Discovery | Reconnaissance | 0/thirteen | ✕ |
| Lateral Movement | Actions on Objectives | v/9 | ✓ |
| Collection | Actions on Objectives | 0/five | ✕ |
| Command and Control | Command and Control | 8/13 | ✓ |
| Exfiltration | Actions on Objectives | 0/eight | ✕ |
| Impact | Deportment on Objectives | i/1 | ✓ |
Table 2. Execution of malicious code without any encryption method.
Tabular array 2. Execution of malicious code without any encryption method.
| AV/Test | A | B | C | D | E | F | Chiliad | H | I |
|---|---|---|---|---|---|---|---|---|---|
| PandaDome 20.01.00 | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ | ✕ | ✓ |
| BitDefender 1.0.17.221 | ✕ | ✕ | ✓ | ✓ | ✓ | ✓ | ✕ | ✓ | ✓ |
| TrendMicro 16.0 | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Sophos 10.viii.ten.810 | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | ✓ |
| Karspersky 21.two.16.590 | ✓ | ✕ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Avast 21.i.2443 | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ | ✕ | ✓ |
| AVG 20.10 | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ | ✕ | ✓ |
| Avira 15.0.2101.2070 | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ |
| Eset fourteen.0.22.0 | ✕ | ✕ | ✓ | ✓ | ✓ | ✓ | ✕ | ✓ | ✓ |
| BullGuard 21.0.387 | ✕ | ✕ | ✕ | ✓ | ✓ | ✓ | ✕ | ✕ | ✓ |
| EBDS | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
Tabular array 3. Execution of malicious code modified using AES encryption.
Table 3. Execution of malicious code modified using AES encryption.
| AV/Test | A | B | C | D | Due east | F | H |
|---|---|---|---|---|---|---|---|
| PandaDome 20.01.00 | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | ✕ |
| BitDefender 1.0.17.221 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| TrendMicro 16.0 | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | ✓ |
| Sophos 10.viii.10.810 | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | ✕ |
| Karspersky 21.2.xvi.590 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Avast 21.1.2443 | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ |
| AVG 20.ten | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ |
| Avira fifteen.0.2101.2070 | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | ✕ |
| Eset 14.0.22.0 | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | ✕ |
| BullGuard 21.0.387 | ✕ | ✕ | ✓ | ✓ | ✓ | ✓ | ✓ |
| EBDS | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
Table four. Execution of malicious lawmaking modified past applying string exchange.
Table 4. Execution of malicious lawmaking modified by applying cord exchange.
| AV/Exam | A | B | C | D | E | H |
|---|---|---|---|---|---|---|
| PandaDome 20.01.00 | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ |
| BitDefender 1.0.17.221 | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ |
| TrendMicro 16.0 | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ |
| Sophos 10.eight.10.810 | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ |
| Karspersky 21.2.16.590 | ✓ | ✕ | ✕ | ✓ | ✓ | ✓ |
| Avast 21.1.2443 | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ |
| AVG xx.x | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ |
| Avira 15.0.2101.2070 | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ |
| Eset 14.0.22.0 | ✕ | ✕ | ✕ | ✓ | ✓ | ✓ |
| BullGuard 21.0.387 | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ |
| EBDS | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
Table five. Execution of malicious code modified using XOR encryption.
Table five. Execution of malicious lawmaking modified using XOR encryption.
| AV/Test | A | B | C | D | H |
|---|---|---|---|---|---|
| PandaDome xx.01.00 | ✕ | ✕ | ✕ | ✕ | ✕ |
| BitDefender one.0.17.221 | ✕ | ✕ | ✓ | ✓ | ✓ |
| TrendMicro sixteen.0 | ✕ | ✕ | ✕ | ✕ | ✕ |
| Sophos ten.viii.10.810 | ✕ | ✕ | ✕ | ✕ | ✕ |
| Karspersky 21.2.16.590 | ✓ | ✕ | ✓ | ✓ | ✓ |
| Avast 21.1.2443 | ✕ | ✕ | ✕ | ✕ | ✕ |
| AVG twenty.10 | ✕ | ✕ | ✕ | ✕ | ✕ |
| Avira 15.0.2101.2070 | ✕ | ✕ | ✕ | ✓ | ✕ |
| Eset 14.0.22.0 | ✕ | ✕ | ✓ | ✓ | ✓ |
| BullGuard 21.0.387 | ✕ | ✕ | ✓ | ✓ | ✓ |
| EBDS | ✓ | ✓ | ✓ | ✓ | ✓ |
| Publisher's Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and atmospheric condition of the Creative Eatables Attribution (CC By) license (https://creativecommons.org/licenses/by/4.0/).
Source: https://www.mdpi.com/2076-3417/12/3/1076/htm
0 Response to "Review on the Application of Artificial Intelligence in Antivirus Detection System"
Post a Comment